The Internet Needed HTTPS—Blockchains Need an Encryption Layer
It might be difficult to imagine now, but the success of the Internet was not always guaranteed. In the early days, there was email, blogs, and websites, but the vision of the Internet espoused by early visionaries was a long way off being realized.
Today, we take things like online shopping, banking, and the sharing of sensitive data for granted, but the early Internet had none of these use cases. It was missing a key component: security.
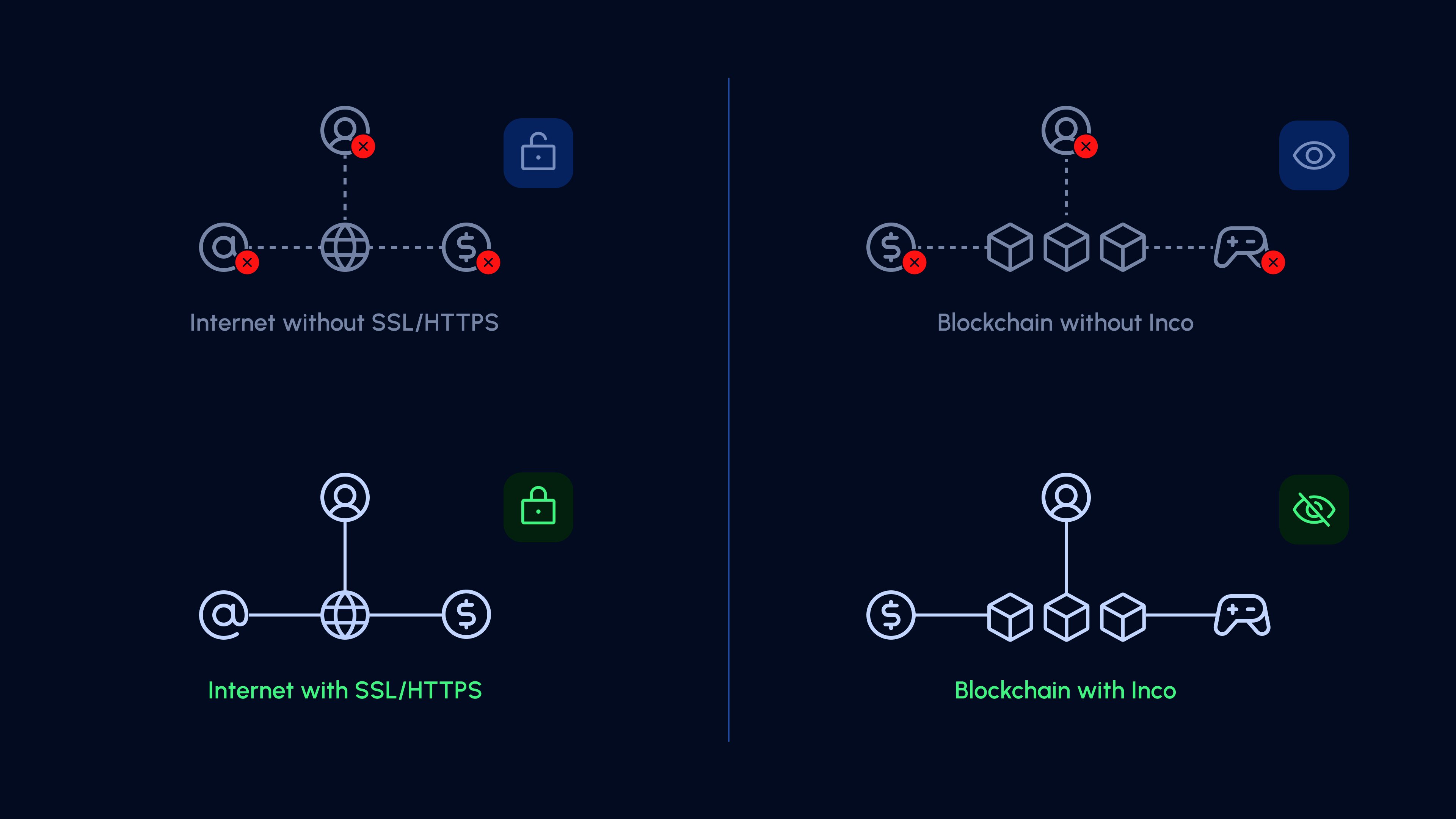
That changed with the invention of HTTPS. First introduced in 1994 by Netscape, HTTPS is an extension of HTTP (Hypertext Transfer Protocol) and uses encryption protocols such as SSL (Secure Sockets Layer) and TLS (Transport Layer Security) to secure data transfers between a user's browser and the server. When a user connects to a website, the server sends a digital certificate to verify its identity, and both the browser and server create a shared encryption key. This ensures that any data sent between them is encrypted, helping protect it from interception or tampering.
Before HTTPS, users were reluctant to enter their bank details into a website for fear they might be leaked to a third party. Today, this isn’t something we have to think about. With secure banking, ecommerce, and communication—all powered by HTTPS and its associated protocols—the adoption and use of the Internet grew exponentially.
There’s a similar challenge at play today. Blockchains have added a trustless, decentralized value layer to the Internet, enabling users to transact without third parties and offering a universal, shared backend for the global economy. However, more than a decade after their introduction, there are still many use cases that have yet to be realized, and many members of the wider public—along with global institutions—have been reluctant to adopt the technology despite its clear promise.
One of the key reasons for this is the lack of confidentiality. Public blockchains provide transparent ledgers that enable trust and verification among participants, but to combine these qualities with the utility of the centralized Internet, they require an upgrade. Users need to be able to send tokens without their transactions being visible to the entire network—companies won’t begin to pay their employees onchain in large numbers if anyone can see how much each team member is getting paid. And large-scale adoption by financial institutions requires the ability for them to offer confidentiality—an investment bank would be unlikely to issue a bond onchain if the amount held by each investor was transparent to the public.
Just as HTTPS made the internet a trusted environment for sensitive interactions like banking and e-commerce, encryption-based methods such as Fully Homomorphic Encryption (FHE) and Trusted Execution Environments (TEEs) could similarly transform blockchains by enabling secure, private transactions without sacrificing the transparency and decentralization that make blockchains unique. HTTPS allowed the internet to move from a space of public, read-only data to a platform for secure, interactive transactions. Encryption-based approaches have the potential to do the same for blockchains, protecting sensitive information without disrupting the decentralized trust that powers them.
The Confidentiality Revolution
Traditionally, efforts to introduce confidentiality to blockchains have focused on zero-knowledge cryptography and other commitment-based approaches, which provide advanced privacy, making them ideal for use cases such as private peer-to-peer transactions. However, they faces challenges with composability.

While commitment-based approaches can be valuable components of blockchain privacy, alone they are insufficient to create an encryption stack that enables a fully decentralized, onchain counterpart to HTTPS/SSL.
So, can we find a method that serves the same function HTTPS does for blockchains?
Solving the Blockchain Confidentiality Problem
Encryption-based methods offer a solution to the blockchain confidentiality problem, with recent research and technological advancements creating a means to provide confidentiality to blockchains without compromising on composability or developer/user experience. Several technologies can be used and then combined with other technologies to create an enryption stack that complements existing blockchains.
Trusted Execution Environments (TEEs)
What if you could keep select data hidden in an environment you could all-but guarantee was private and secure while still being able to run functions on it? This is the concept behind TEEs. TEEs provide an isolated execution environment that protects both code and data from the rest of the system. The data is decrypted within the TEE, meaning it can be computed upon and processed while staying secret and secure. All parties can verify that the compute has been completed as intended and has not been tampered with.
Fully Homomorphic Encryption (FHE)
Historically, it has been a core assumption that data must be decrypted in order to be computed upon. This creates a foundational limitation for processing data, as security and confidentiality risks are introduced whenever data requires processing. Data is most often computed on secure servers, but data leaks and security vulnerabilities are common. But what if decryption wasn’t necessary in order to compute upon data?
In 1978, Ronald Rivest, Leonard Adeleman, and Michael Dertouzos introduced the concept of privacy homomorphisms, which could enable computations on encrypted data without revealing information about the underlying plaintext. While this idea was revolutionary, their initial schemes could only support a restricted set of operations on encrypted data—for example, you could do addition or multiplication, but not both—rendering them impractical for most real-world use cases.
After decades of continued research, in 2009, cryptographer Craig Gentry made a breakthrough by solving a major issue in homomorphic encryption. Previously, computations on encrypted data would gradually accumulate errors, much like how a photocopy of a photocopy becomes less clear with each copy. Gentry's solution, called 'bootstrapping,' allowed the system to reset itself and reduce these errors, making it possible to perform unlimited computations on encrypted data without losing accuracy.
Subsequent work by the cryptographic community has addressed efficiency and performance issues, resulting in a current manifestation that can solve many of the security and confidentiality challenges previously thought inherent to online activity.
The Foundations of the Blockchain Encryption Layer
Things get really exciting when we combine these encryption methods with blockchain technology. On a public blockchain like Ethereum, TEEs and FHE would mean that data could be added to the network in ciphertext form, opaque to the public, but still be computed upon, with developers able to run functions on it and build apps using it. Such an approach enables features that were, until now, impossible to achieve at the same time: decentralization, utility, and confidentiality.
A wide range of use cases becomes possible by combining these features. For example, in healthcare, patient data could be securely shared and analyzed by multiple institutions without exposing sensitive medical records. In supply chains, companies could track shipments and verify product authenticity without revealing confidential business data to competitors. Just as HTTPS enabled secure transactions in e-commerce and banking, this approach could power a wave of blockchain adoption in industries that require both transparency and confidentiality.
Where Inco Fits In
So how do we combine these technologies and blockchains in practice? We have the encryption methods and we have public blockchains, but how do we turn them into a blockchain standard just as HTTPS/SSL became the standard for the Internet?
That’s where Inco comes in. Inco is a modular computing network that combines TEEs and FHE with Zero-Knowledge Proofs (ZKPs) and Multi-Party Computation (MPC) to enable confidential computation for any blockchain.
Inco is designed to make the integration of confidentiality as seamless as possible for developers. By providing an encryption-enabled version of the Ethereum Virtual Machine, developers can immediately begin building confidential blockchain applications using the same tools they’re already familiar with, like Solidity, MetaMask, Remix, and Hardhat. This means there's no need to learn new languages or frameworks—developers can focus on building the future of private, decentralized applications using the tools they know best.
A developer looking to build an onchain poker game on Ethereum could store the core game logic on the Ethereum network and offload features that require confidentiality, such as each player’s hand of cards, to the Inco network, enabling this data to be computed and used to run the game while ensuring it isn’t exposed to other players.
Encryption-based approaches providee the missing piece blockchains have been lacking: confidentiality. With confidentiality available to any developer on existing blockchains through the tools they’re already comfortable with, we’re about to see a plethora of new use cases be brought onchain, with a wave of adoption similar to the post-HTTPS wave of adoption seen by the centralized Internet in the 1990s.
To learn more about Inco and the use cases you can build by leveraging the confidentiality it provides, check out the Inco documentation.
Incoming newsletter
Stay up to date with the latest on FHE and onchain confidentiality.
.svg)